Network Miner
NetworkMiner is an open source Network Forensic Analysis Tool (NFAT) for Windows (but also works in Linux / Mac OS X / FreeBSD). NetworkMiner can be used as a passive network sniffer/packet capturing tool to detect operating systems, sessions, hostnames, open ports etc. without putting any traffic on the network. NetworkMiner can also parse PCAP files for off-line analysis and to regenerate/reassemble transmitted files and certificates from PCAP files.
NetworkMiner has, since the first release in 2007, become a popular tool among incident response teams as well as law enforcement. NetworkMiner is today used by companies and organizations all over the world."
Network Miner in Forensics
The ultimate goal of network forensics is to provide sufficient information to detect malicious activities, security breaches, and network anomalies based on the network traffic. And NetworkMiner is a great tool to help, as it provides quick and useful hints on where to start from, specifically:
Context of captured hosts like their IP and MAC, hostnames, or OS information
List of potential attack indicators or anomalies like traffic spikes or port scans
Tools or toolkits used to perform the potential attacks like Nmap
Supported Data Types
There are three main data types investigated in Network Forensics:
Live Traffic
Traffic Captures
Log Files
NetworkMiner in a Nutshell
Capability
Description
Traffic sniffing
It can intercept the traffic, sniff it, and collect and log packets that pass through the network.
Parsing PCAP files
It can parse pcap files and show the content of the packets in detail.
Protocol analysis
It can identify the used protocols from the parsed pcap file.
OS fingerprinting
File Extraction
It can extract images, HTML files and emails from the parsed pcap file.
Credential grabbing
It can extract credentials from the parsed pcap file.
Clear text keyword parsing
It can extract cleartext keywords and strings from the parsed pcap file.
Operating Modes
There are two main operating modes:
Sniffer Mode: Although it has a sniffing feature, it is not intended to use as a sniffer. The sniffier feature is available only on Windows. However, the rest of the features are available in Windows and Linux OS. Based on experience, the sniffing feature is not as reliable as other features. Therefore we suggest not using this tool as a primary sniffer. Even the official description of the tool mentions that this tool is a "Network Forensics Analysis Tool", but it can be used as a "sniffer". In other words, it is a Network Forensic Analysis Tool with but has a sniffer feature, but it is not a dedicated sniffer like Wireshark and tcpdump.
Packet Parsing/Processing: NetworkMiner can parse traffic captures to have a quick overview and information on the investigated capture. This operation mode is mainly suggested to grab the "low hanging fruit" before diving into a deeper investigation.
Pros and Cons
As mentioned in the previous task, NetworkMiner is mainly used to gain an overview of the network. Before starting to investigate traffic data, let's look at the pros and cons of the NetworkMiner.
Pros
OS fingerprinting
Easy file extraction
Credential grabbing
Clear text keyword parsing
Overall overview
Cons
Not useful in active sniffing
Not useful for large pcap investigation
Limited filtering
Not built for manual traffic investigation
Differences Between Wireshark and NetworkMiner
NetworkMiner and Wireshark have similar base features, but they separate in use purpose. Although main functions are identical, some of the features are much stronger for specific use cases.
The best practice is to record the traffic for offline analysis, quickly overview the pcap with NetworkMiner and go deep with Wireshark for further investigation.
Feature
NetworkMiner
Wireshark
Purpose
Quick overview, traffic mapping, and data extraction
In-Depth analysis
GUI
✅
✅
Sniffing
✅
✅
Handling PCAPS
✅
✅
OS Fingerprinting
✅
❌
Parameter/Keyword Discovery
✅
Manual
Credential Discovery
✅
✅
File Extraction
✅
✅
Filtering Options
Limited
✅
Packet Decoding
Limited
✅
Protocol Analysis
❌
✅
Payload Analysis
❌
✅
Statistical Analysis
❌
✅
Cross-Platform Support
✅
✅
Host Categorisation
✅
❌
Ease of Management
✅
✅
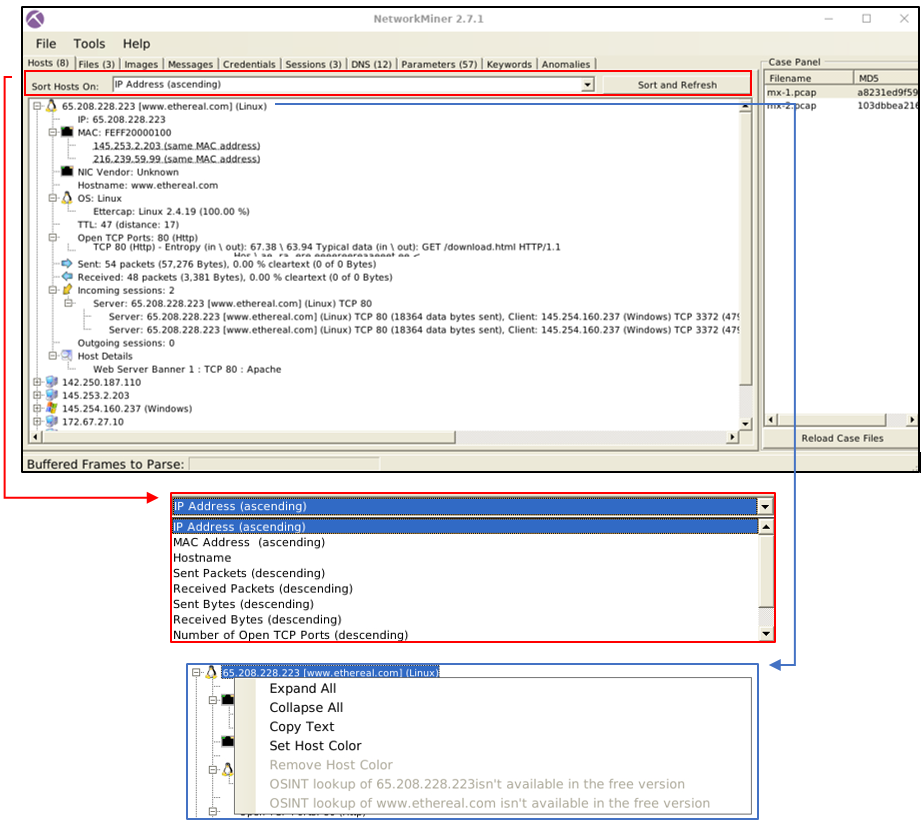
Hosts
The "hosts" menu shows the identified hosts in the pcap file. This section provides information on:
IP address
MAC address
OS type
Open ports
Sent/Received packets
Incoming/Outgoing sessions
Host details
OS fingerprinting uses the Satori GitHub repo and p0f, and the MAC address database uses the mac-ages GitHub repo.
You can sort the identified hosts by using the sort menu. You can change the colour of the hosts as well. Some of the features (OSINT lookup) are available only in premium mode. The right-click menu also helps you to copy the selected value.
Sessions
The session menu shows detected sessions in the pcap file. This section provides information on:
Frame number
Client and server address
Source and destination port
Protocol
Start time
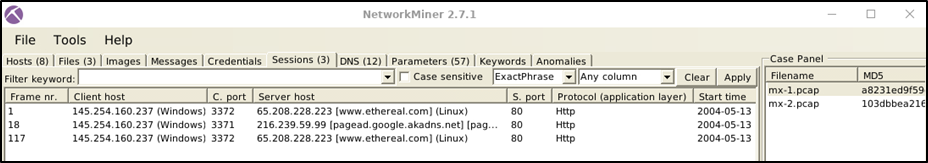
You can search for keywords inside frames with the help of the filtering bar. It is possible to filter specific columns of the session menu as well. This menu accepts four types of inputs;
"ExactPhrase"
"AllWords"
"AnyWord"
"RegExe"
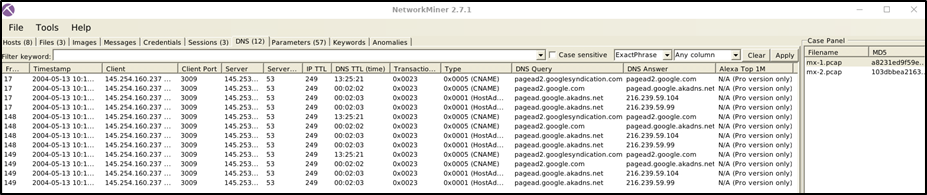
DNS
The DNS menu shows DNS queries with details. This section provides information on:
Frame number
Timestamp
Client and server
Source and destination port
IP TTL
DNS time
Transaction ID and type
DNS query and answer
Alexa Top 1M
Some of the features (Alexa Top 1M) are available only in premium mode. The search bar is available here as well.
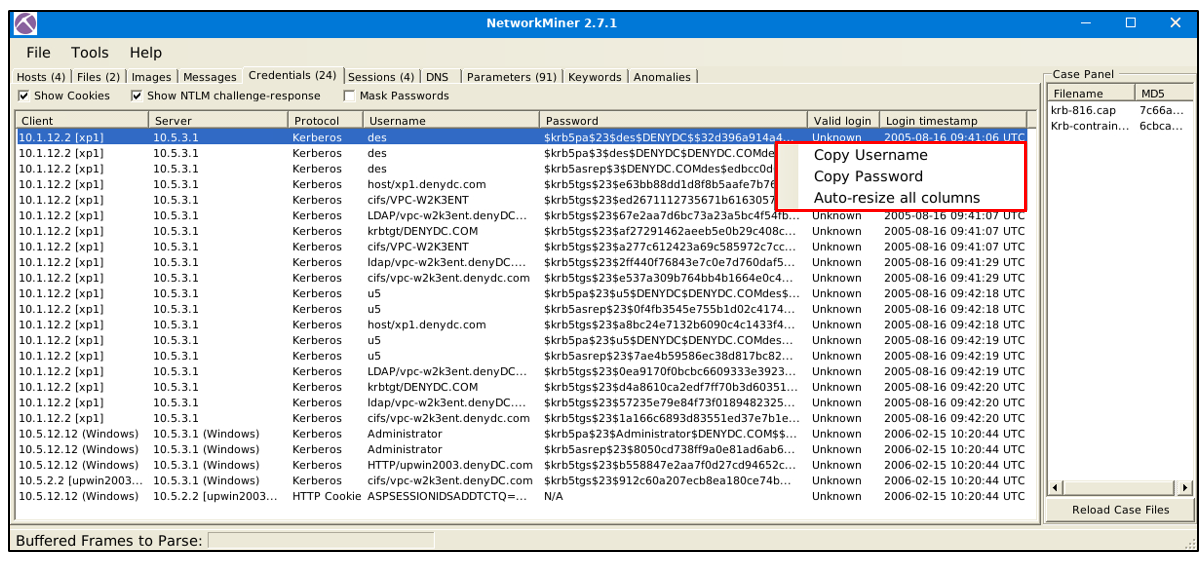
Credentials
The credentials menu shows extracted credentials and password hashes from investigated pcaps. You can use Hashcat (GitHub) and John the Ripper (GitHub) to decrypt extracted credentials. NetworkMiner can extract credentials including:
Kerberos hashes
NTLM hashes
RDP cookies
HTTP cookies
HTTP requests
IMAP
FTP
SMTP
MS SQL
The right-click menu is helpful in this part as well. You can easily copy the username and password values.
Last updated